Cool Tips About How To Check For Conficker

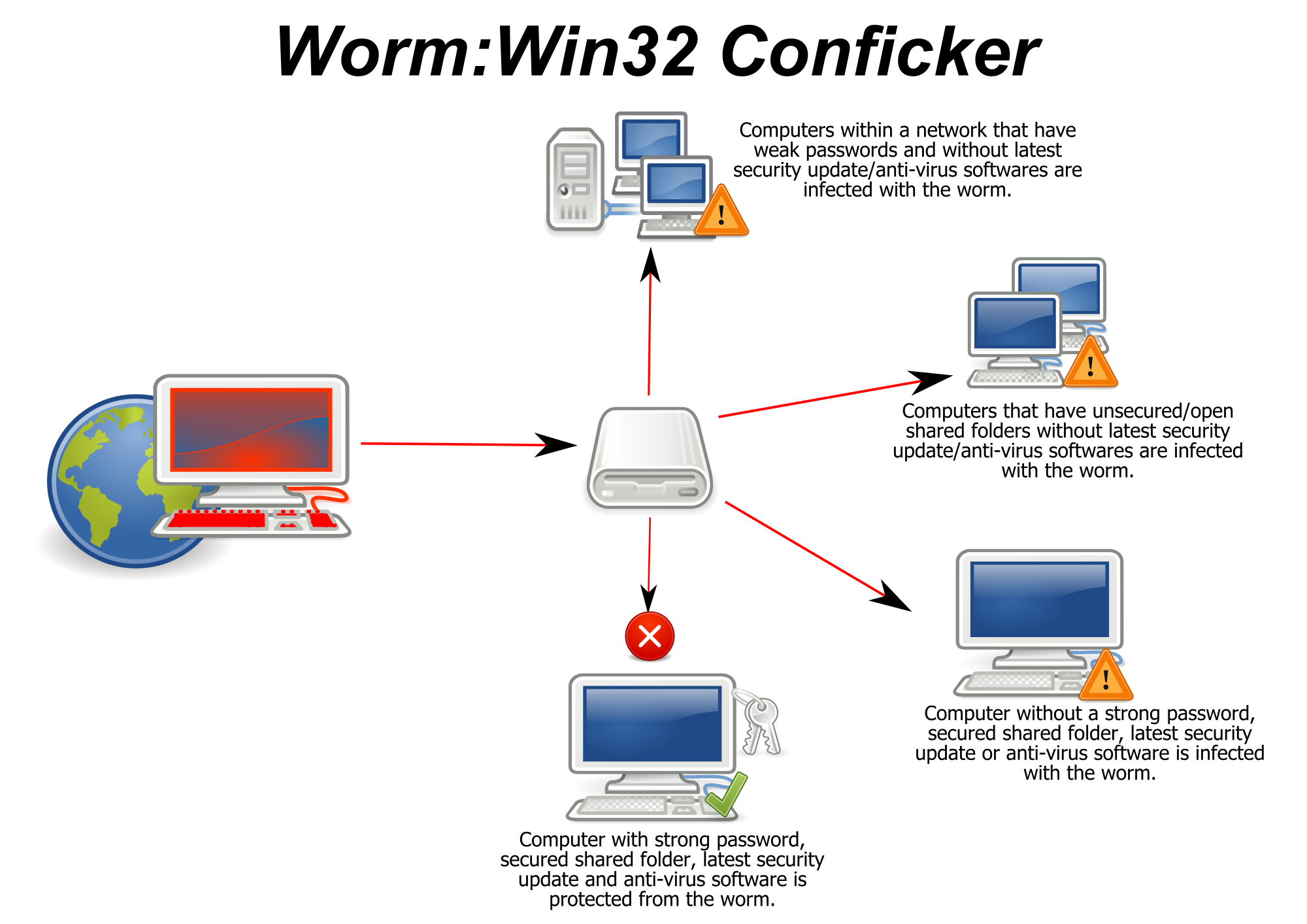
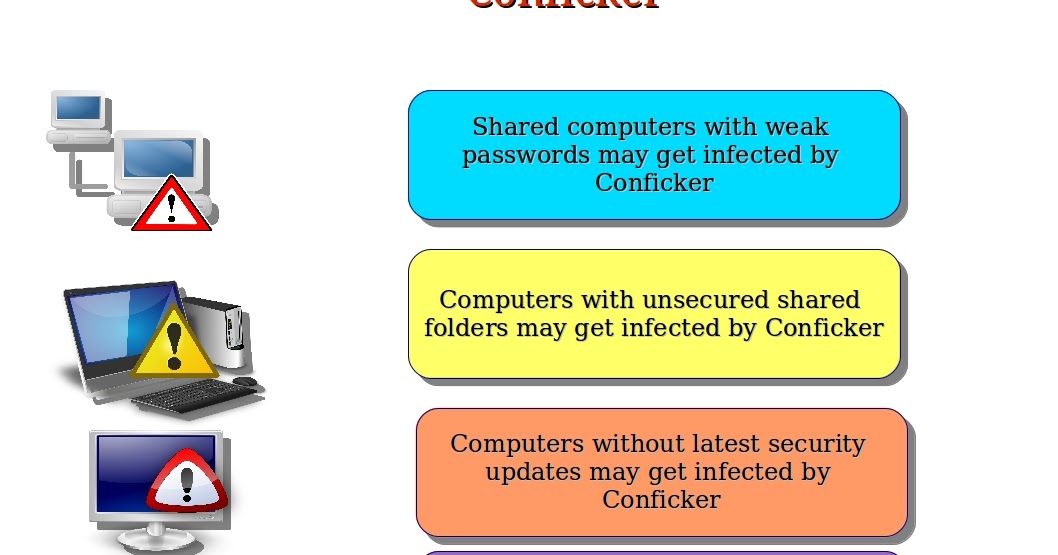
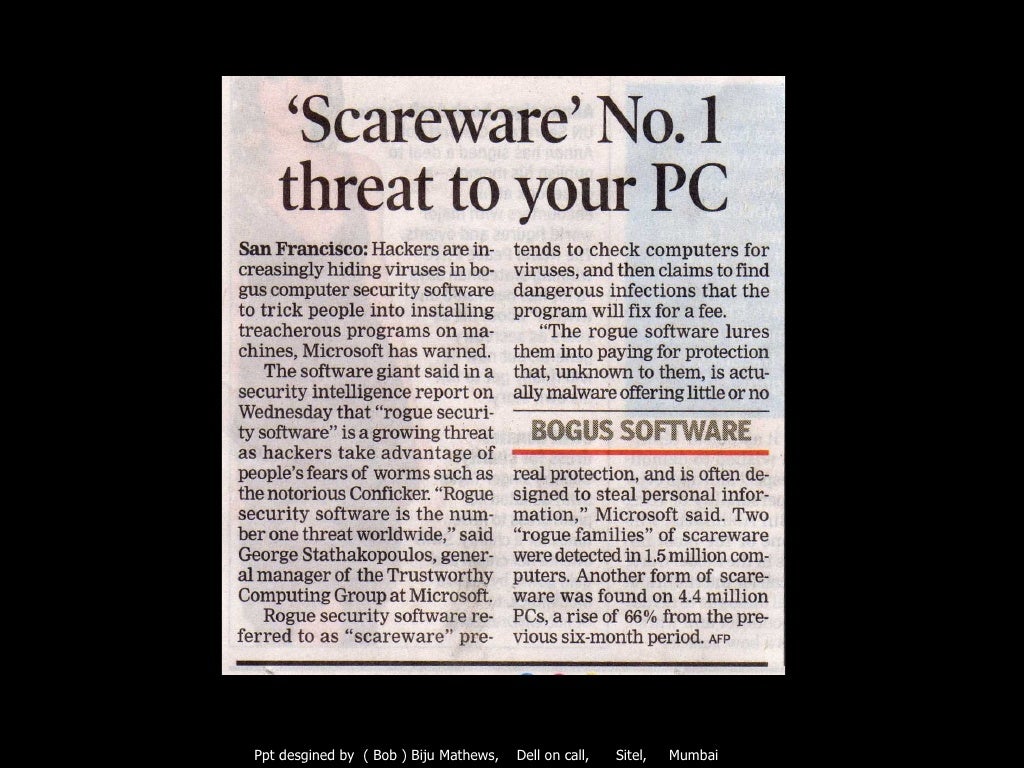
Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008.
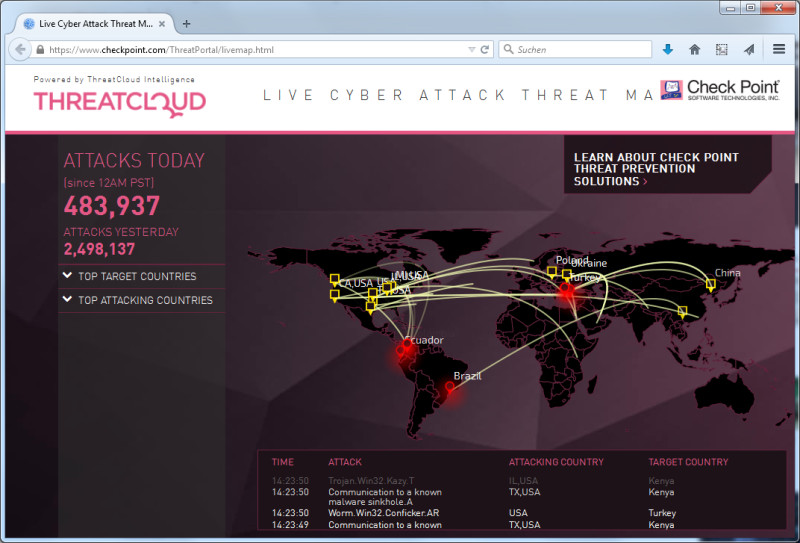
How to check for conficker. Eset conficker checker and removal tool : Security event logs network monitoring tools firewalls with logging (i.e.,. There are a few tools that you can use to track and find conficker infected computers on your network.
Check for internet connectivity by attempting to connect to one of the following sites: Conficker malware writers made use of domain names rather than ip addresses to make their attack networks resilient against detection and takedown. Windows 2000, widnows xp, windows server 2003 overall risk rating:
When conficker.c or higher infects a system, it opens four ports: Checks if a host is infected with conficker.c or higher, based on conficker's peer to peer communication. 5 the latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445 services on infected machines.
Here is what you need to look for in regards to conficker. Likely clean |_ regsvc dos:. 6 answers sorted by:
How does the conficker virus work? Steps to configure the dns sinkhole action, see: A quick visual scan can tell you whether you're infected with the conficker worm or similar malware.
Also known as downadup, conficker was.




:max_bytes(150000):strip_icc()/how-to-write-a-check-4019395_FINAL-eec64c4ad9804b12b8098331b5e25809.jpg)